My BSides Belfast 2019 Talk: Offensive Ansible for Red teams Attack, Build, Learn

BSidesBelfast (October 31st 2019) was the first time that I actually presented at a major conference.
I've been to quite a few other BSides events, but always as an attendee, never as a speaker. That all changed when I got the opportunity to present a talk on 'Offensive Ansible for Red Teams - Attack, Build, Learn'.
Overall, it was an incredible first experience that will be hard to forget. The Titanic Centre venue was great - a wonderful building in itself to experience, let alone the Titanic themed tours. Well worth a visit indeed.

Early start
I had arrived just before 8am - plenty of time, given that I wasn't speaking until 11.45. Not many hackers seem to like 8am starts - I was expecting a huge queue to get in, but that wasn't the case.
In the elevator to the 5th floor location for the event, I bumped into Brian Honan who was giving the key note speech at 9am. I wanted to check out the Olympic Suite - where I was presenting at 11:45am and sure enough, none other than Cooper (a.k.a. 'Ministraitor') was getting his recording rigs setup.
The Keynote & The Talks
The theme for Brian Honan's opening keynote was 'Back to Future' - no matter how much things change with new technologies, his basic premise was that the same attacks that are happening, albeit with new technology.
Get the simple stuff right such as decent passwords, patching etc and don't be so worried about the latest and greatest zero days. I would have to strongly agree with him there - even as a Red Teamer, I always prefer to go for the low hanging fruit first. These are the basic table stakes that people need to get right first.
In terms of the actual talks there were a few standout items for me personally. Martin Lee's 'Building the Best Team to Hunt the Biggest Threats' was very insightful. Even though I'm a Red Team Operator, I'm always interested to hear about how defense teams (and more specifically, threat hunters) actually work. It's the job of a Red Team to probe the security capabilities of an enterprise and to ultimately help it develop a more mature security posture.
Joakim Kennedy delivered a great malware based talk 'The Joule Thief: A Look Into the Activity of "the Cryptominer Champion" Rocke'. I'm fascinated by the rise of malware created with the 'go' (a.k.a 'golang') language, which is partly due to the fact that 'go' binaries are statically compiled and can be generated for multiple platforms. Very handy.
And of course there was the excellent talk on How to investigate iOS devices by Paul Rascagnères (a.k.a.'r00tbsd'). He certainly made quite an entrance (BSides organisers invited people to dress up for Halloween). You can see for yourself here :-)
I was wondering why I somehow missed an interesting talk by Rory Flynn (a.k.a @roolyaboolya), but then I realised that I was actually somewhat busy presenting my own talk! Take a look here for details of Rory's presentation (slides etc).
And then I was up
The MC in the Olympic Suite (where I was presenting) was none other than @bsidesbelfast regular Edwin van Andel (a.k.a '@Yafsec'). We had a very brief chat just before the attendees returned from a morning caffeine refuelling break - just to cover some basic biographical details etc.
Edwin was quite funny addressing the crowd as he introduced me to them. I recognized a few faces in the crowd and so I just assumed that I was presenting to them and few others. I felt at ease, and with that, I was 'off to the races'.
The basic thrust of my presentation was that automation tools such as Ansible can be used offensively from three perspectives: attacking, building and learning. Firstly, attacking - this covered:
- how to determine if a Linux target has Ansible installed
- what host inventories (of more juicy targets) are available to it.
- how to run simple ad-hoc commands to perform some recon, exfiltrate data etc
- how to create what appear to be innocuous looking playbooks to install updates, but are in fact ways to install beacons/reverse shell payloads that report back to some type of C2 mechanism
- how to elevate privileges all the way to Domain Administrator - in fact 'SYSTEM' on a Domain Controller if you want to own everything!
The pre-recorded demos went fine and seemed to grab the attention of the crowd. I was at pains to point out that Ansible in itself was not the issue. However, if an Ansible Controller server is not locked down properly, it will be essentially 'game over' if an attacker gains root access to it.
You can get a sense of that in the screenshot below, where I showed how Ansible can be weaponized to deliver a payload to machines in an inventory, which results in gaining a system level shell. In this specific case, I had system level privs on a Windows 2012 R2 Domain Controller - i.e. I 'owned' the entire domain!
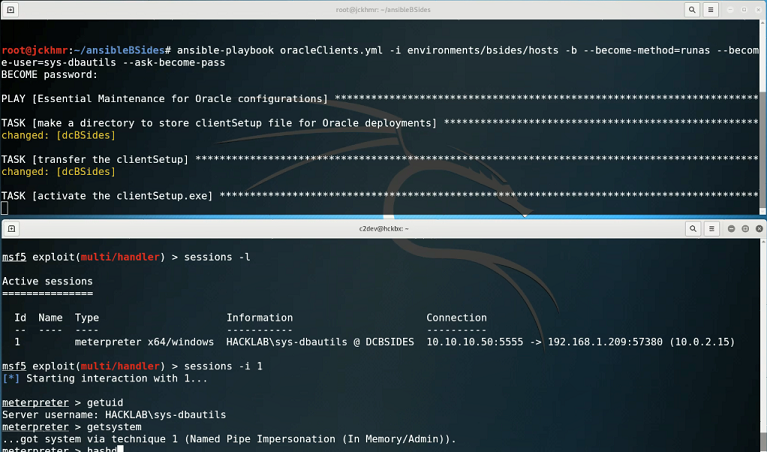
Yes - I know that in a proper Red Team scenario you probably wouldn't use a Meterpreter based executable, but you get the idea of just how badly things can go wrong if a server designated as an Ansible controller is poorly secured.
For the 'learn' part of my talk I wanted to show how through tools such as Vagrant and Ansible, that it is possible to set up a lab on a local computer very easily. All of the components can be summarized in the following simplified diagram:
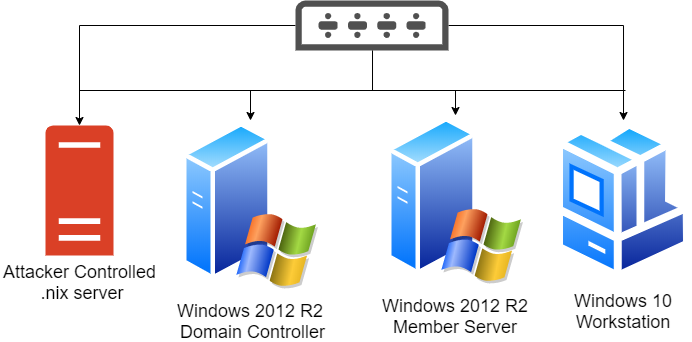
This type of setup is perfect if you just want to learn more about attacking Acitive Directory environments or if you want to model a complex attack scenario before trying on a real target in production (with permission of course!!!!). A pre-recorded video showed how easy it was to run a Vagrant script that pulled down pre-built boxes from VagrantCloud, installed them to VirtualBox and then configured them with Ansible to create a fully functional environment.
Finally, from a 'build' perspective, there was additional coverage on how Ansible could be used (along with Terraform) to create and configure a complete C2 attack environment in the cloud. We all have to learn the hard way to ensure we understand the core concepts, but on a live operation you just want to have access to a working environment to get on with your hacking. In this respect, automation via Ansible and Terraform just works brilliantly - quicker and consistent.

My timing was pretty much spot on, the demos went well and I got some interesting questions from the crowd. It was one hell of a buzz to have gone through the whole experience.
I had some nice feedback from folks at the conference, both in person and via twitter, which is sincerely appreciated. It certainly gave me a taste for doing more of this sort of stuff - I've marked a few potential conferences for 2020 to submit talk proposals for.
The Swag ....
The @bsidesbelfast crew always deliver on really nice t-shirts, but as a speaker I also got a really nice hoodie and a speaker 'challenge coin' too - very cool indeed. The hoodie is also very practical for this time of year - thanks a million for it! I also managed to acquire a few other t-shirts and obligatory stickers to add to my growing collection. However, my wife put me straight that collecting t-shirts/hoodies at a conference does NOT constitute as going shopping. Nice try Leo.

Summing Up
I may of course be biased, but I felt that BSidesBelfast 2019 was a great experience - the location in itself can accommodate a lot more people than was previously possible at the Europa Hotel in Belfast city centre.
There were certainly a great variety of talks on offer - and I've watched some of the videos up on YouTube. In terms of the overall experience quality, I've been to @BSidesDublin and @BSidesMcr in 2019 and Belfast is right up there with both.
It takes a hell of a lot of time and effort to put these sorts of shows on, so kudos to everyone at @BSidesBelfast for this!
As I mentioned earlier, watch out for a follow-up article that will be a deep-dive into all the bits and pieces behind all things Ansible and Vagrant, with some recommendations to other folks who are looking to dip their toes into preparing for their first conference talk.
I'm only just getting started ...di

